The Security Tapestry Cybersecurity Operations Platform
Crafted by security professionals for security professionals, our Cloud-Native XDR/SIEM and Security Log Management solutions are tailored to meet your security needs.
An innovative approach: Managed SOC
The Security Tapestry Cybersecurity Operations Platform offers the industry’s most comprehensive cloud-native solutions for detecting, investigating, and responding to threats. With a cloud-scale architecture, our security log management swiftly ingests, parses, stores, and searches data. Behavioral analytics establish baselines for user and device behaviors using histograms to detect and prioritize anomalies based on risk. Our automated investigation streamlines the IR workflow, providing a holistic threat view, automating manual tasks, and simplifying complex processes.

Compliance and Certifications
Operating national and global organizations entails compliance with international laws, and Security Tapestry is your partner in meeting these global compliance needs. We have implemented robust technical and organizational measures to align with GDPR requirements and offer resources to assist you in fulfilling commitments to your customers and safeguarding their personal data.
At Security Tapestry, our Governance, Risk, and Compliance team is committed to upholding a secure operational landscape for your sensitive data. Our stringent internal zero-trust policy, continuous security awareness training, and routine third-party security assessments exemplify our dedication to ensuring the utmost security for our valued customers.
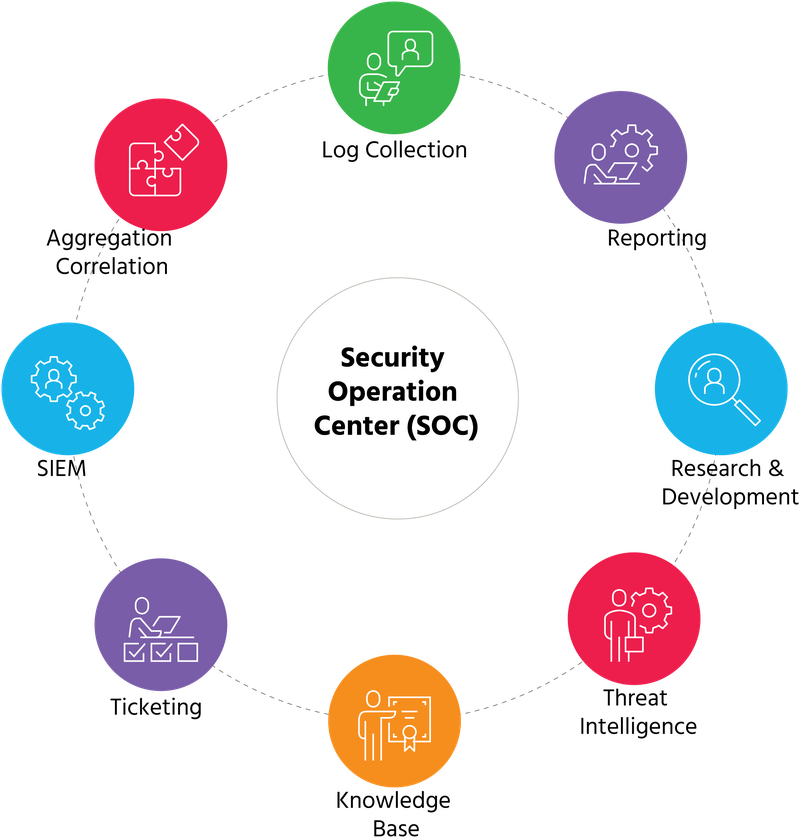
Data Collection
Gather data effortlessly from a wide array of sources, including over 200 on-premises products, 30+ cloud-based security solutions, and 20+ cloud infrastructure offerings from the top three industry-leading cloud infrastructure providers.
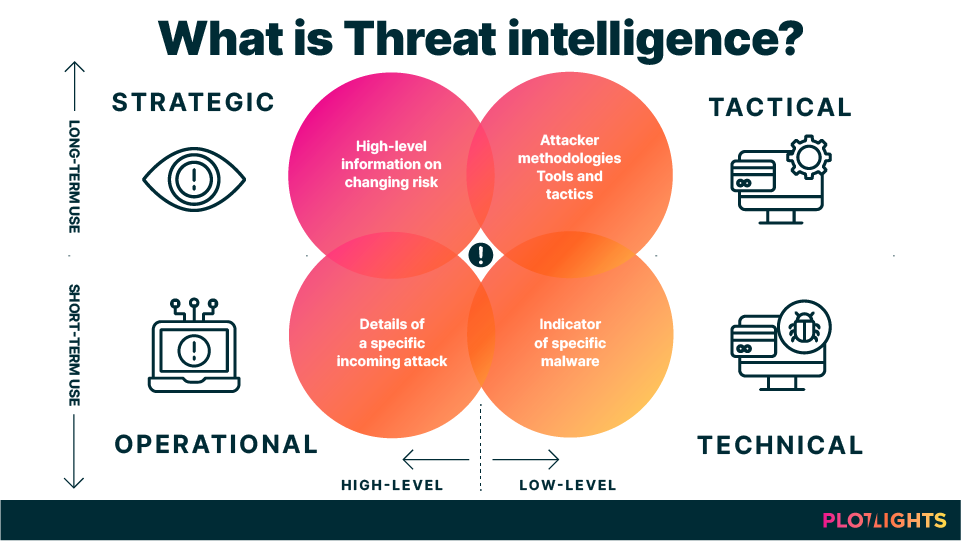
Advanced Threat Intelligence
Available with all Security Tapestry products, our Threat Intelligence Service enhances event context by incorporating information from various commercial and open-source threat intelligence feeds. It then gathers, cleans, and assesses this data, utilizing our proprietary machine learning algorithms to generate a consistently accurate and current stream of IoCs (Indicators of Compromise).
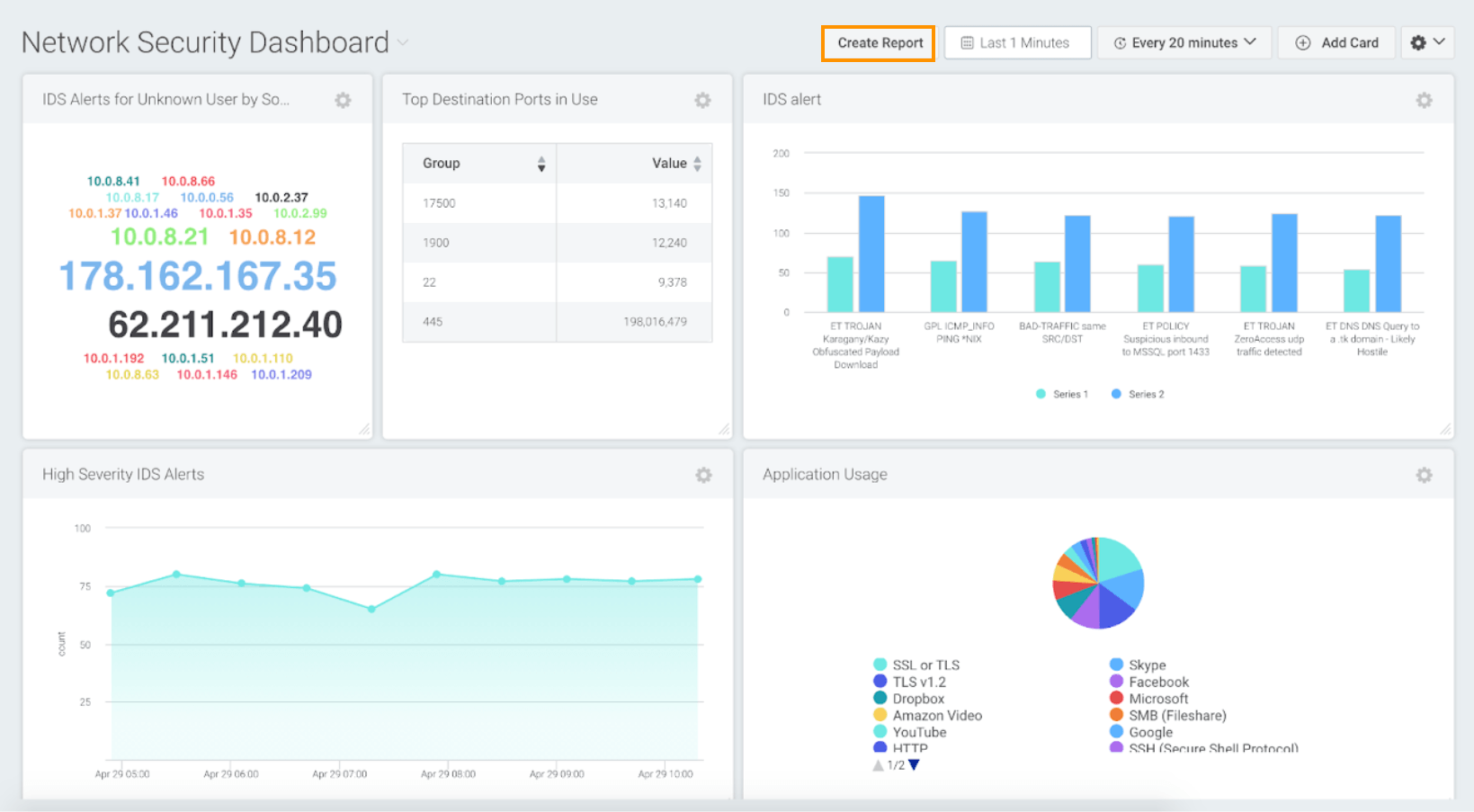
Dashboard and Reporting
Easily manage your dashboard data by printing, exporting, or viewing it with a variety of reporting options. Our offerings include pre-built compliance reports, tailor-made reports, and diverse dashboards featuring 15+ unique chart types.
Our customers have the flexibility to select one or multiple visuals that align with their specific business requirements. These visual options encompass bar charts, column charts, line graphs, area charts, pie charts, donut charts, bubble charts, funnels, single values, sankey maps, word clouds, heat maps, tables, Coverage Maps, and more.

MITRE ATT&CK® Coverage
The Security Tapestry Cybersecurity Operations Platform employs the ATT&CK framework as a crucial perspective to enhance your security posture’s visibility. Our support for ATT&CK extends across all 14 categories, encompassing 200+ techniques and 400+ sub-techniques within the ATT&CK framework
Context Enrichment
Context enrichment delivers substantial benefits across multiple aspects of our platform. Security Tapestry supports three enrichment methods: threat intelligence, geolocation, and user-host-IP mapping. Our Threat Intelligence Service equips you with the latest IoCs, enhancing your data with file, domain, IP, URL reputation, and TOR endpoint identification. This enrichment helps prioritize and update existing correlations and behavioral models. Geolocation enrichment provides valuable location-based context that is often absent from logs. When it comes to user information, which is typically lacking in logs outside of authentication sources, Security Tapestry’s user-host-IP mapping enrichment bridges the gap by adding crucial user details to the logs, facilitating the construction of behavioral models for the detection of anomalous activities.
300+
Integrations
Gather data from a vast array of over 600 product integrations spanning 300+ distinct vendors.
15+
Unique Dashboard Charts
Multiple Dashboard types to give your organization the highest-level view of data possible
14
MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 200+ techniques and 400+ sub-techniques.
Ready to enhance your cybersecurity strategy?
Connect with us today to set up an initial conversation with our Security Tapestry experts. Discover how our tailored security solutions can make a difference for your organization.
